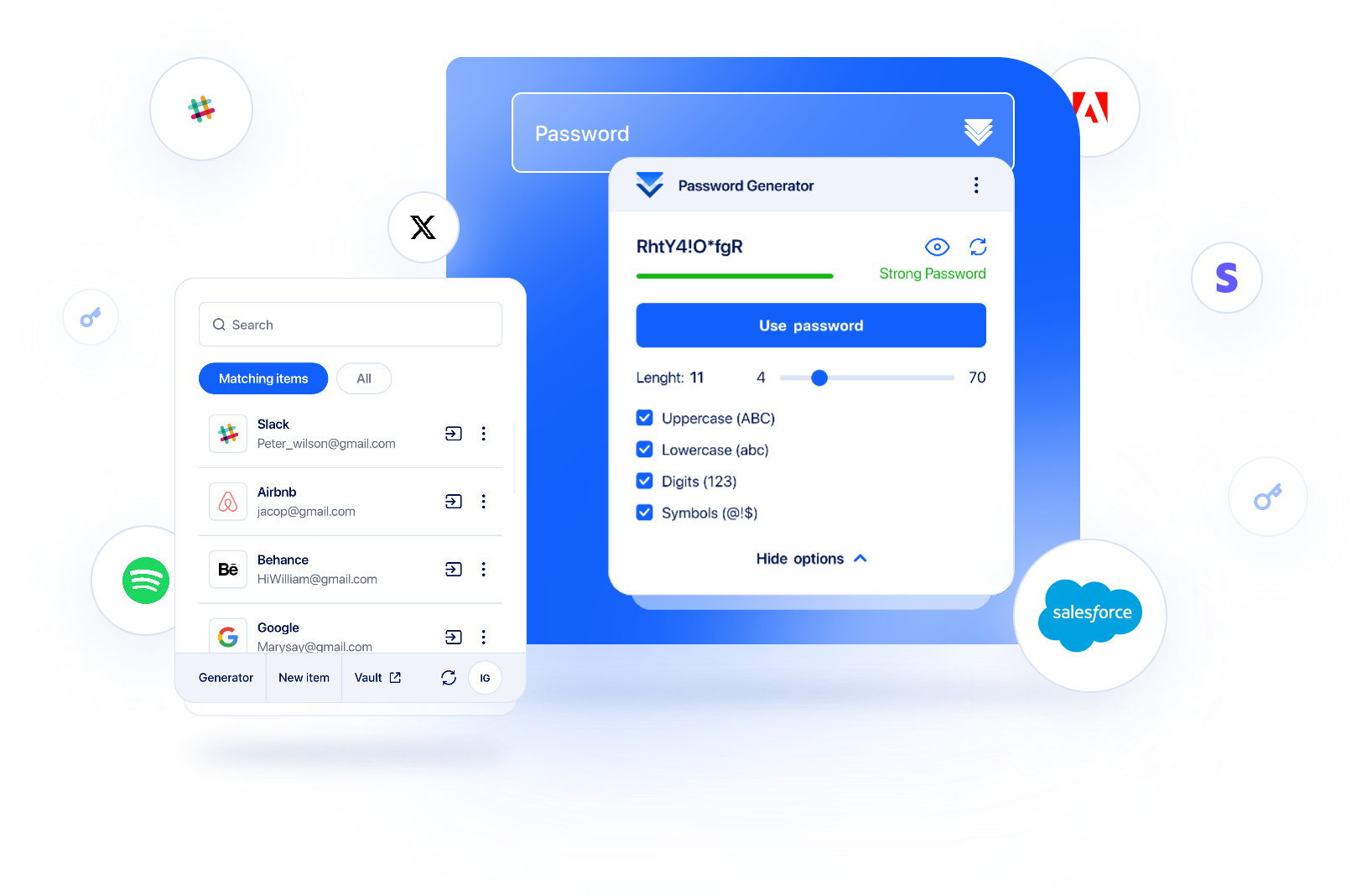
Swiss security, protected by the strictest data privacy laws
TransferChain is a company based in Switzerland. While our team operates from various parts of the world, our headquarters are located in Zug, Switzerland. While Swiss legislation is politically neutral, it also enforces some of the most stringent data privacy regulations globally.